What’s wrong with in-browser cryptography?
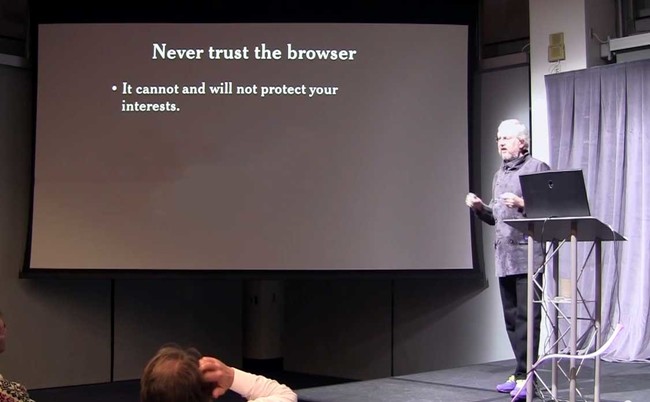
Above image taken from Douglas Crockford’s Principles of Security talk
If you’re reading this, then I hope that sometime somebody or some web site told you that doing cryptography in a web browser is a bad idea. You may have read “JavaScript Cryptography Considered Harmful”. You may have found it a bit dated and dismissed it.
You may have read about WebCrypto and what it hopes to bring to the browser ecosystem. This particular development may make you feel that it’s okay to start moving various forms of cryptography into the browser.
Why not put cryptography in the browser? Isn’t it inevitable? This is a perpetual refrain from various encryption products which target the browser (names and addresses intentionally omitted). While the smarter ones try to mitigate certain classes of attacks by shipping as browser extensions rather than just a web site that a user types into their...