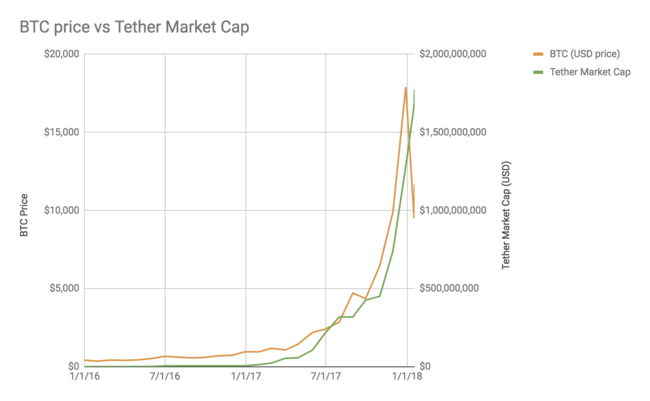
Rust 2020: towards a 1.0 crate ecosystem
The Rust language itself went 1.0 in 2015. And yet, almost 5 years later, at least in my anecdotal assessment talking to and reading things written by current or potential users, there is still a sense that the language is still in some way unfinished and a bit rough around the edges.
I sympathize with these concerns.
There are various language-level issues which are partly to blame for this. The absence of a comprehensive story around asynchronous I/O and event-driven programs in general has been one of them, but that all changes… today… with the long awaited stabilization of async/await in the Rust 1.39 release along with the release of futures v0.3.0 earlier this week.
There are other core features which many desire. In my Rust in 2019 blog post I wrote about const generics as the 1 in my top 3, along with async/await and Pin, which both shipped this year.
Others long for even...